
Cybersecurity is not something to be taken lightly. It’s only when it’s too late that many businesses realize just how vital online security really is.
By using the official NIST cybersecurity framework, sanctioned by the US Government, Calsoft has been able to help businesses keep their operations safe and secure.

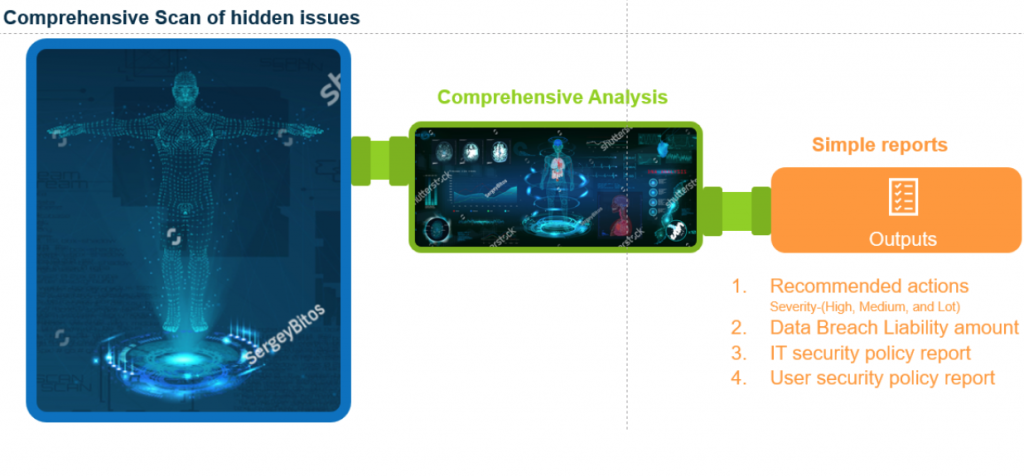
Comprehensive Reports
IT Assessment’s benefit is that our client can obtain our IT security policy report and user security policy report.

Actionable Tasks
Some IT managers know there are some issues the company’s network has. But the managers do not know appropriate counteractions to prevent the actual incident from happening around the issues.

Comprehensiveness
Our NIST-based approach and the physical assessment provide the comprehensiveness of the IT system risk assessment. This is the essential benefit of the service.
Optimize Your Return on Investment
Calsoft IT Assessment Deliverables
It is always difficult to measure the severity of issues and risks quantitatively.
How much damage does an incident that one accounting employee stores the company credit card number in her company PC’s memory and an attacker has access to the number?
How much damage all potential issues altogether have to the client company?
Calsoft has the solution to this. Client management would make better management decisions based on the quantitative risk impact.
Calsoft’s report provides a data breach liability amount for each potential incident.
Our client loves our recommended actions. We organize the action into high, medium, and low severity. Our client knows where to start from the next day to mitigate future cybersecurity risks.

IT Assessment Case Study
Our client CEO did not know where to start while he faces thick security report data that is not human-readable. This was a typical situation that companies face even if they use a vendor to analyze the situation.
The vendors leave with incomprehensive reports. Our client faced increasing demand from its parent company that it proactively acts toward cybersecurity risks. While the client company did not have a dedicated IT manager to lead this requirement, they approached Calsoft.
The client management had an idea of security issues. After Calsoft’s comprehensive assessment, the client was fully aware of its potential risks, high and low severity.
What is NIST?
National Institute of Standards (NIST) is a federal agency within the United States Department of Commerce that was assembled due to Executive Order 13636, issued in 2013. The institute is composed of over 3,000 people from diverse parts of industry, academia, and government.
Their Mission: to develop and promote measurement, standards, and technology to enhance productivity, facilitate trade, and improve the quality of life. NIST is also responsible for establishing computer- and information technology-related standards and guidelines for federal agencies to use.
“It is the policy of the United States to enhance the security and resilience of the Nation’s critical infrastructure and to maintain a cyber environment that encourages efficiency, innovation, and economic prosperity while promoting safety, security, business confidentiality, privacy, and civil liberties.”
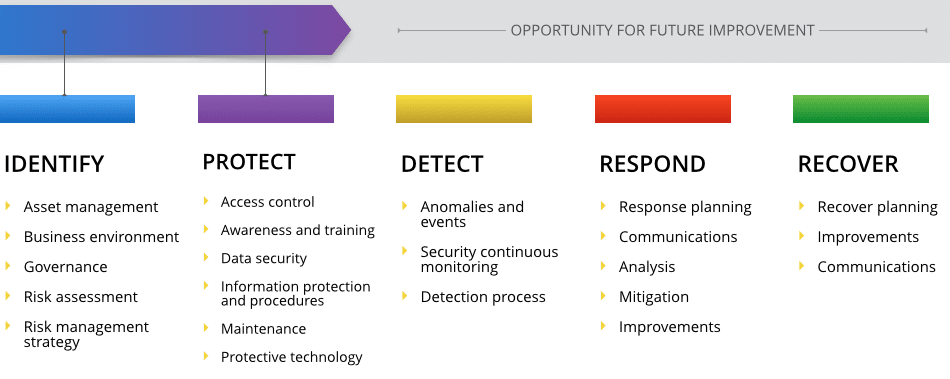
The Framework Core is a set of cybersecurity activities, desired outcomes, and applicable references that are common across critical infrastructure sectors.
Core consists of five concurrent and continuous functions:
-
Identify
-
Protect
-
Detect
-
Respond
-
Recover
More About the NIST Framework
The NIST Framework Core is a set of industry standards, guidelines, and practices executed in a manner that enables secure communication, activities and outcomes throughout an organization.
These functions provide a high-level, strategic view of the lifecycle of an organization’s management of cybersecurity risk assessment.
The risk assessment process identifies underlying key categories and subcategories for each function, and matches them with example informative references, such as existing standards, guidelines, and practices for each subcategory.
Contact
Any questions? Contact a Specialist
OVERVIEW
Five Rules of NIST Framework
1
Identify
Calsoft understands the client’s organization’s mission, objectives, stakeholders, and activities first. Calsoft uses this information to analyze cybersecurity roles, responsibilities, and risk management decisions. Then, Calsoft understands the policies, procedures, and processes to manage and monitor the organization’s regulatory, legal, risk, environmental, and operational requirements. Knowing the client’s assets, we assess the client’s cybersecurity risk. With this cybersecurity risk assessment, the client organization can prioritize both operational and supply chain risk decisions. This clarifies priorities, constraints, risk tolerances, and assumptions of the organization.
2
Protect
The core of the Project step is to manage data security. This begins with Access Control. Authorized users, processes, and devices limit access to physical and logical assets. The organization also needs to provide cybersecurity awareness and training. The organization also needs to manage technical security solutions. While all of these are clear, the organization needs to manage its information and records consistent with its risk strategy to protect the confidentiality, integrity, and availability of information.
3
Detect
The organization maintains and tests anomalous detection processes to ensure awareness of anomalous events. When it detects abnormal activity, the organization needs to understand the event’s impact. The organization responds to the event next.
4
Respond
The organization coordinates its response activities with internal and external stakeholders while it analyzes its response effectiveness. While the organization mitigates the incident, it also needs to prevent incident expansion.
5
Recover
Now after the organization effectively manage the incident, it is time to recover. It needs to execute the recovery process and coordinate restoration activity with other parties. In the end, it is important to improve the recovery plan and process.
WHO WE ARE
The Calsoft Advantage

1000+ Successful Implementations
-
Migrating data over from your Legacy system
-
Maintain your core business process
- 500+ years of experience across the board
-
Industry experience on system guidance: BC/F&SCM

Full IT Lifecycle
-
Assessment, ERP, Network, Security, Training, Support, Upgrades
-
Third party add-on guidance and Project Management
-
Azure Private or Public cloud
-
NIST CSF Certified Engineers

100% Rescue Project Achievement Rate
-
System Usage and Implementation Analysis
-
HelpDesk Support Team on-standby
-
World-Class User Training and Materials
-
Critical Issues Projects
