ERP security is the first step to avoiding a devastating impact on your organization. The fundamental purpose of an ERP system is to collect all business data from various departments into one application to manage business processes better. This holistic approach offers unparalleled insights, facilitating better decision-making and resource allocation. Yet, this convenience comes with a price – the aggregation of sensitive data into one location creates an attractive target for cybercriminals seeking to exploit vulnerabilities.
Recognizing the significance of ERP security is the first step towards fortifying your organization against potential breaches. By implementing comprehensive security measures, you can safeguard your business from the devastating impacts of cyber-attacks.
Understanding the Significance of ERP Data Security
The information and data within ERP software are some of the most critical and sensitive data in a business. From financial records to customer data, supply chain information to production details, an ERP system consolidates a wealth of critical and sensitive information. Data security has become a concern, and businesses have increased their cybersecurity and knowledge to identify and protect against internal and external cyber threats.
The rise in cyber threats and the potential for devastating breaches have prompted organizations to ramp up their ERP cyber security efforts. Recognizing the gravity of the situation, companies are investing in advanced technologies, cultivating a deeper understanding of potential risks, and enhancing their ability to identify and combat internal and external cyber threats.
Human error is the primary cause of so many privacy and data breaches. Accidental data leaks, misconfigured access controls, and inadvertent sharing of sensitive information are just a few examples of the vulnerabilities that can arise due to human actions. Therefore, the responsibility for ensuring the safety of ERP solutions and the data they house extends not only to the ERP providers but also to the users who interact with these systems.
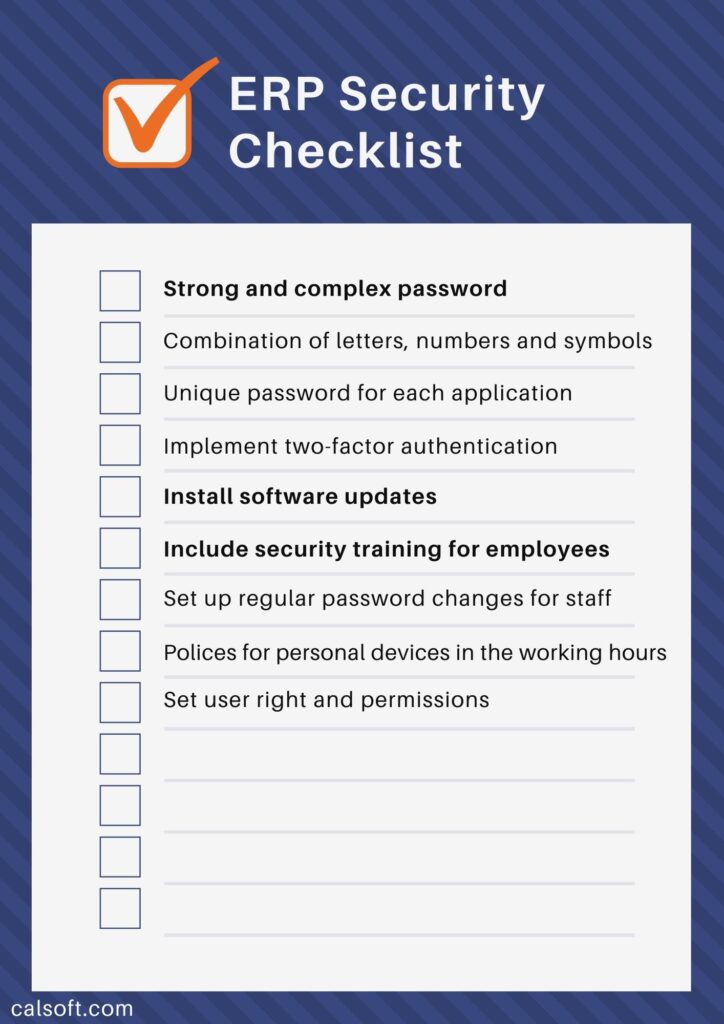
ERP Security Checklist
To keep your ERP protected and secure, it’s critical to establish appropriate controls. Breaches can often be traced back to an internal compromise such as a phishing attack. The potential security risks in ERP software can be reduced by educating employees, having two-step verification and more frequent software and security updates. Here are some ERP security best practices:
- Strong and complex password
- Use a combination of letters, numbers and symbols
- Create a unique password for each application
- Implement two-factor authentication (2FA)
- Install software updates
- Regularly installing ERP software updates addresses weaknesses that have been identified in the software. Cyber threats constantly change and hackers keep finding new ways to get around security, therefore installing the latest software update is vital for higher security.
- Include security training for employees
- Set up regular password changes for staff
- Create polices to avoid using personal devices in the working hours
- Review user rights and permissions regularly to ensure that company data is only available for selective staff access
- Harness the power of cloud ERP
- Cloud-based ERP systems offer built-in security measures
- Automated detection of suspicious activity
Read more: 9 Simple Cyber Security Rules To Remember
Benefits of cloud ERP
With cloud ERP, the costs of managing security are much lower because it is included in the subscription from the ERP provider. Cloud providers have installed and maintained specialized systems for automated detection of suspicious activity.
Is Cloud ERP secure?
This is a question often asked by ERP users and business owners. As businesses explore the advantages of cloud-based solutions, the question of whether Cloud ERP is secure remains a pertinent one. While Cloud ERP systems do indeed adhere to robust security standards, it’s essential to recognize that ensuring data protection requires a multi-faceted approach.
Cloud ERP systems have gained prominence for their flexibility, scalability, and ease of access. They offer the convenience of anytime, anywhere access to critical business data, driving efficiency and collaboration. Cloud ERP systems come with good security standards, and are typically hosted on secure data centers, where providers invest heavily in advanced security technologies, compliance certifications, and dedicated teams to safeguard their infrastructure.
However, the security of Cloud ERP doesn’t solely rest on the shoulders of the providers. Organizations that adopt Cloud ERP still need to implement additional controls around security like creating ERP secure login, user access, updating software and training employees.
Read more: 7 Ways Cloud ERP Helps You Reduce Risk
How secure is Dynamics 365?
All of Microsoft’s cloud based products, including ERP systems like Dynamics 365 Business Central and Dynamics 365 Finance and Operations are hosted on their own cloud platform Azure.
Microsoft also operates the Microsoft Cyber Defense Operations Center which is a cybersecurity and defense facility controlled by security experts and data scientists that work to protect Microsoft’s cloud infrastructure, detecting and responding to threats 24/7. Microsoft invests over $1 billion a year in protecting the security of their users and their data information.
Read more: Dynamics 365 Security
Dynamics 365 security model
Dynamics 365 provides an efficient role-based security framework to ensure data confidentiality at all levels with well-defined security roles and access controls. You can structure your data access authorizations, rights, and restrictions based on their user level.
Users of D365 Business Central are assigned a profile that reflects their business role, the department they work in, or another categorization. Profiles allow administrators to define and manage centrally what different user types can see and do in the user interface so they can perform their business tasks efficiently.
The D365 Business Central security system allows you to control which objects a user can access within each database or environment. You can specify for each user whether they are able to read, modify, or enter data in the selected database objects.
In Business Central, there are two levels of permissions to database objects:
- Overall permissions according to the license, also referred to as the entitlement.
- More detailed permissions as assigned from within Business Central.
The five access levels supported by Dynamics 365 security model are:
- Global – Access to all records held by the organization
- Deep – Access to all records under a business unit and child units
- Local – Access to all records within a business unit
- Basic – access to data records within a team
- None – No access permitted
User privileges are categorized into seven types:
- Create — user is able to add a new record
- Read — user is able to view a record
- Write — user is able to edit a record
- Delete — user is able to delete a record
- Append — user is able to connect or associate other entities with a parent record
- Append to — user is able to connect or associate other entities with a record
- Assign — user is able to give ownership of a record to another user
- Share — user is able to give access to a record to another user
Each of these privileges can be assigned different levels of access, restricting which entities they apply to depending on ownership, and location within the business.
Read more: Dynamics 365 Benefits: 5 Advantages of Having ERP from Microsoft
Conclusion
Data security is not just a technical concern; it’s a critical aspect that directly impacts on the reputation and integrity of your company.
As businesses continue to digitize and rely on cloud-based solutions like Cloud ERP, maintaining a strong security posture becomes essential. While Cloud ERP providers uphold stringent security standards, it’s the collective effort of both providers and organizations that fortifies the protective layers around sensitive information.
By adopting ERP security best practices such as ERP secure login mechanisms, stringent user access controls, and regular software updates, organizations can significantly reduce the risk of data breaches and cyber incidents. These measures bolster the integrity of the Dynamics 365 security model, ensuring that only authorized individuals can access, manipulate, and manage your company’s invaluable data.
Understanding the importance of user roles within the Dynamics 365 security model is equally vital. Different roles demand distinct levels of access to ensure the right people have the appropriate permissions while minimizing the potential for unauthorized data exposure. This approach to role-based access control optimizes data security, maintaining a delicate balance between accessibility and protection.
If you have questions about ERP security or Dynamics 365 security model, contact us today. Our team is dedicated to assisting you in configuring a robust ERP security framework tailored to your business needs. Whether you’re seeking guidance on user roles, encryption protocols, compliance requirements, or incident response planning, we’re here to provide the expertise and support you need.

